Single Sign-On
SINAI supports Single Sign-On (SSO) using SAML 2.0, allowing users to securely authenticate through their organization's identity provider.
Configuring SAML-based SSO with SINAI
SINAI supports Single Sign-On (SSO) using the SAML 2.0 protocol, allowing your organization to manage user authentication through your existing identity provider (IdP). This guide walks you through the configuration process for setting up SAML-based SSO with SINAI.
Overview
With SAML-based SSO, your users can authenticate using your corporate identity provider. Once configured, users attempting to log into SINAI will be automatically redirected to your IdP for authentication, enabling a secure and seamless login experience.
This integration allows your organization to enforce its own security policies—including multi-factor authentication (MFA), IP restrictions, session length, and user access control (e.g., active vs. inactive users)—directly through your identity provider.
How it works
When users navigate to SINAI, they will be prompted to enter their email address:
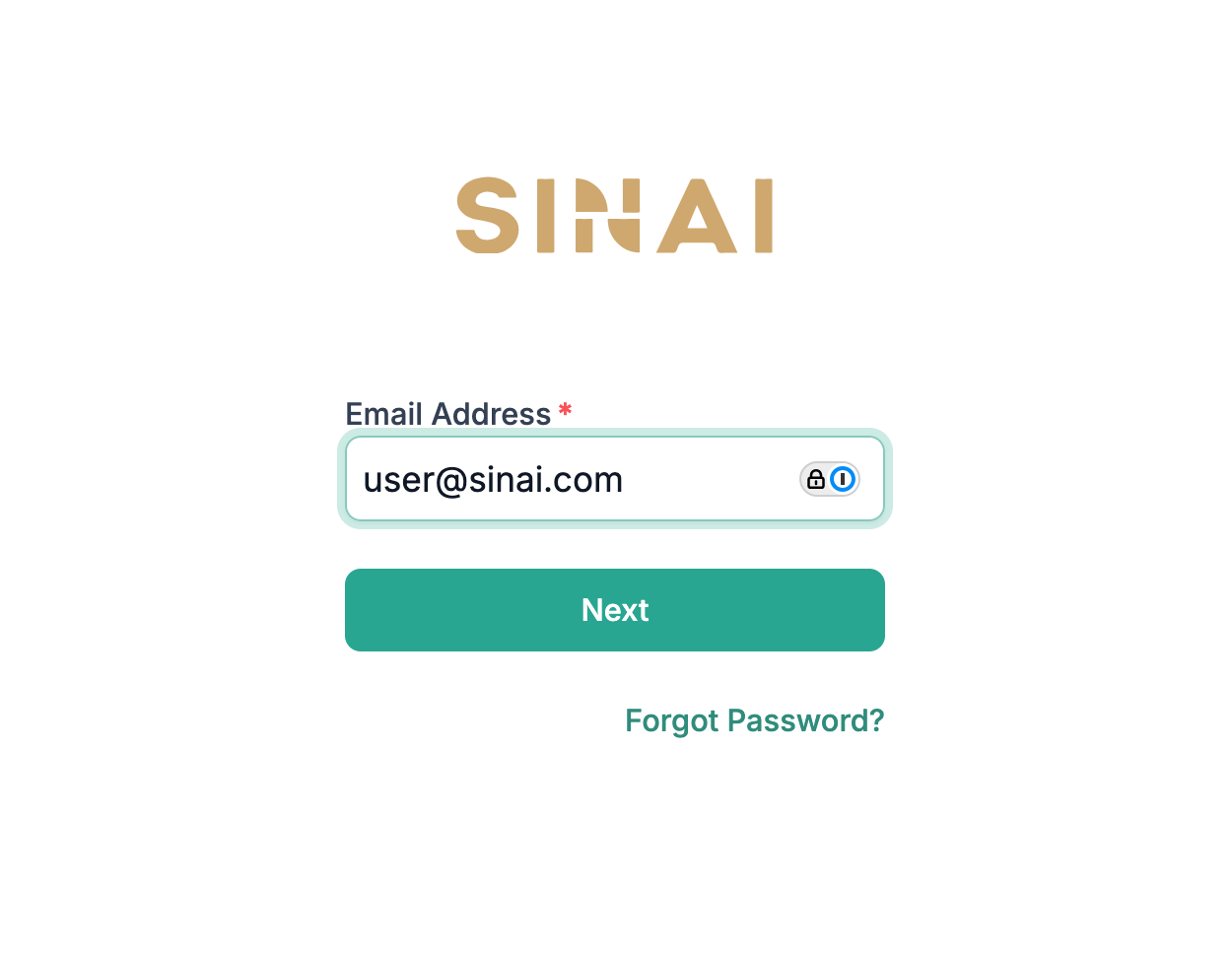
If the email domain is configured for SAML-based SSO, the user will automatically be redirected to your organizations identity provider:
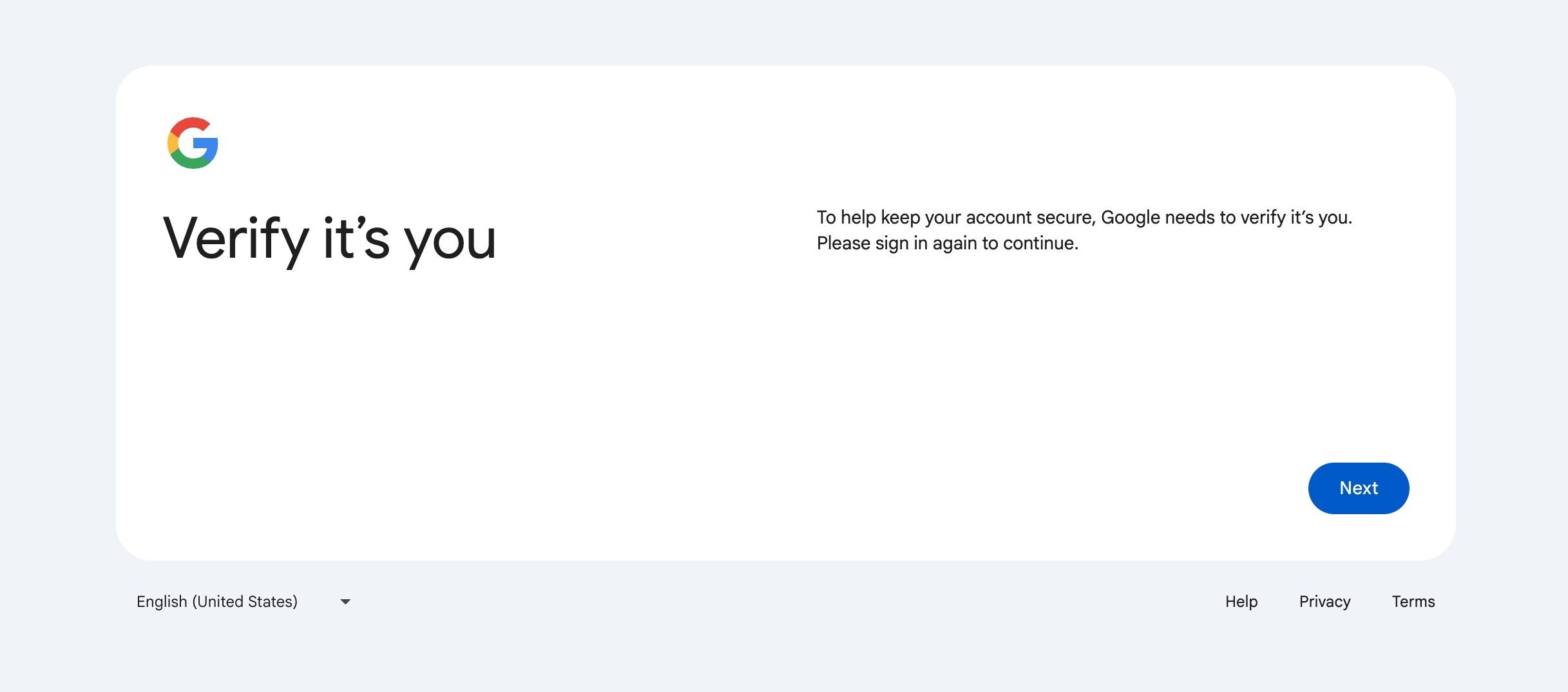
After signing in to your organization's identity provider, the user will be redirected back to the SINAI platform.
Step-by-Step Setup Guide
1. Share Identity Provider Configuration with SINAI
To initiate the setup, please provide either of the following:
- A SAML XML Metadata document, or
- A link to your IdP’s hosted SAML metadata file (if available)
This metadata should contain:
- IdP Entity ID
- SAML SSO URL (Login URL)
- X.509 Certificate (Base64-encoded)
- (Optional) SAML Attributes Mapping, if custom attributes are used (e.g.,
email,firstName,lastName)
Please send this information securely to your SINAI integrations contact.
2. Receive Service Provider Details from SINAI
Once we receive your IdP configuration, the SINAI team will respond with the necessary Service Provider (SP) metadata, including:
- SP Entity ID
- Assertion Consumer Service (ACS) URL
- Required SAML Attributes
This information enables you to establish SINAI as a trusted SAML application within your IdP.
3. Configure SINAI as an Application in Your IdP
Within your identity provider (e.g., Okta, Azure AD, OneLogin, etc.), create a new SAML 2.0 application using the SP metadata provided by SINAI.
- Assign appropriate users or groups who should have access to the SINAI platform.
- Ensure that required attributes such as email address are mapped properly.
- Optionally configure automatic user provisioning if your IdP supports it.
4. Enable SSO in SINAI
Once your configuration is complete, notify SINAI’s integrations team. We will validate the connection and enable SSO on your tenant.
After activation:
- Users will be redirected to your IdP when accessing the SINAI login page.
- Upon successful authentication, users will be redirected back to SINAI and automatically logged in.
Frequently Asked Questions
What identity providers are supported?
Any SAML 2.0-compliant identity provider is supported. This includes (but is not limited to):
- Okta
- Microsoft Azure AD
- Google Workspace
- OneLogin
- Ping Identity
Can we configure Just-In-Time (JIT) provisioning?
Yes. If your IdP supports sending user attributes upon login, SINAI can create user accounts dynamically. Please coordinate attribute mapping and provisioning preferences with the SINAI integrations team.
How do we test the setup?
SINAI allows testing the configuration using a sandbox setup, in order to verify configuration and user access.
Need Help?
If you need assistance at any point in the configuration process, contact the SINAI integrations team or your SINAI sales representative.
Updated 8 months ago